Mosaic Regressor: Second known UEFI Malware
Coming across advanced and devious malware is quite common for researchers from security firm Kaspersky but it is quite rare that they have seen anything like Mosaic Regressor. This is the second known UEFI-based malware that was brought into notice by the latest blog post by the company. This UEFI Malware has extreme system access and staying in command as the malware operates on the low-level boot manager that underlies most modern computers. But there is good news for you that you need not worry about the issue of getting infected.

What is UEFI?
The motherboard is the home of the Unified Extensible Firmware Interface (UEFI) as it resides there on the computer. It is the primary or the first thing which needs to be turned on when you boot up the system and this allows you to get permission to access almost every part of the operating system. And its persistence is still vigilant after reboots or formats or even system component replacements. One of the major issues with UEFI is that it lives or resides on a flash memory chip soldered to the board which makes it even hard to inspect for malware and even harder to purge.
UEFI malware is a way in which you can own the system and reduce the likelihood of getting caught. And getting malicious code into UEFI systems is a difficult problem to administer. But still, an integrated special firmware scanner was provided by Kaspersky into its antivirus products in 2019 and now the firms discovered a Mosaic Regressor, which is the second known instance of UEFI malware.
Where was Malware Formed?
Just two computers of the diplomatic officials in Asia were infected by the malware, according to discovery. The malware allows the attackers to load multiple modules to control the target system and steal data as it includes a full exploit chain that is long and varied and it starts with the help of the UEFI loader. Whenever you boot your system, Mosaic Regressor traverses for its malicious file “IntelUpdate.exe” file is in the Windows startup folder.
If there is no such file found while traversing, it will add the file. And this file is the gateway to all the other mischievous activities Mosaic Regressor can do. Kaspersky was only able to capture a handful of the malware modules and was not able to know the full extent of the operation’s capabilities. Mosaic Regressor is confirmed by the team that it can infiltrate documents from the affected system.
Is China Creator of Malware?
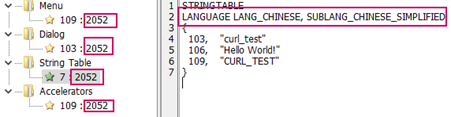
The source of the attack on the diplomat’s computers appears to come from a Chinese-speaking individual or group and it is believed that it could be a tool developed by the Chinese government. And it is still a mystery to Kaspersky that how was the original UEFI code altered. But logical guesses were made by their team based on the knowledge on a piece of 2015 UEFI malware that physical access was needed to the machine to make the exploit possible.
And it is quite unlikely to see this infection to spread through the targets. It would appear like a movie that it is suggested, an intelligence agency orchestrated a professional operation and it is rare to find out the confirmation of this possibility ever.
