Microsoft’s Windows Hello facial recognition feature in Windows 10 and Windows 11 has a vulnerability, according to researchers at CyberArk Labs. As per the researchers, hackers may get around Windows Hello by using a custom-made USB device to eventually gain access to your computer, which they refer to as a “design flaw.”
Though it isn’t easy to do (and Microsoft claims to have patched the vulnerability), there are a few scenarios that can lead to bypassing. Hackers would need to take an infrared image of the victim’s face in all cases, have physical access to the victim’s PC, and employ a bespoke USB device that can imitate a camera. The six-part procedure is described on CyberArk Labs’ website, which also includes a video of the proof-of-concept.
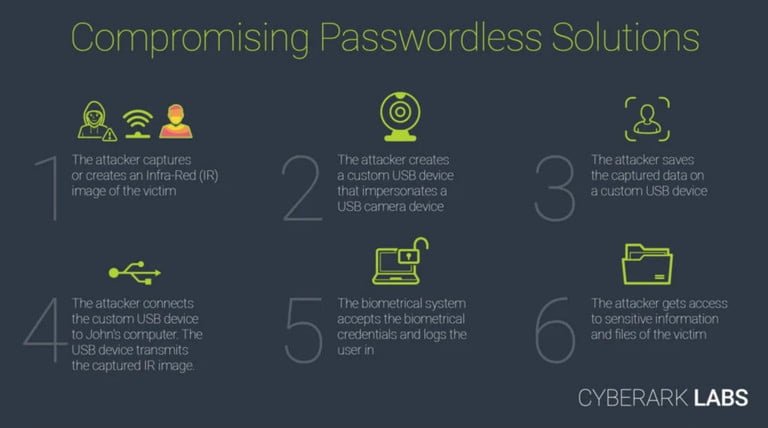
According to the company, This is achievable since Windows Hello only processes IR camera frames when attempting to verify a user. “A USB camera that supports RGB and IR cameras would be required. To bypass the login step, this USB device just has to provide real IR frames from the victim, while the RGB frames can include anything,” CyberArk’s Omer Tsarfati explained.
Although there is no evidence that this flaw has been actively exploited, CyberArk Labs warns that someone with the correct skills could use it to target journalists and others who have sensitive data on their devices. It’s also worth noting that the study focused on Windows Hello for Business rather than the consumer version of the software. However, there’s still a risk that this flaw may affect other security systems that use a third-party USB camera as a biometric sensor.
On March 23, 2021, CyberArk labs reported this vulnerability to Microsoft. A day later, Microsoft recognized the problem. Microsoft has since issued a CVE to the problem and released mitigation in a July 13 security update.
According to Microsoft, this addressed the problem, and Windows Hello Enhanced Sign-in Security can defend against similar attacks. However, CyberArk reminds us that the mitigation is contingent on having devices with specific cameras and that the “inherent to system design, implicit trust of peripheral device input” persists. An investigation is currently being carried out.
