Researchers from the Singapore University of Technology and Design have discovered a set of 20 vulnerabilities known as BrakTooth that affect over 1,400 products based on 13 different Bluetooth devices sold by 11 of the world’s largest suppliers.
1,400 cellphones, computers, keyboards, headphones, and other Bluetooth-enabled devices have been proven to be affected by security flaws. But that’s the absolute minimum. “So because BT stack is frequently shared across numerous products,” the researchers concluded, “it is quite likely that many other items (beyond the 1400 entries detected in the Bluetooth listing) are affected by BrakTooth.”
According to reports, BrakTooth can be used to launch denial-of-service (DoS) attacks and allow arbitrary code execution (ACE) on target devices. DoS attacks can cause the victim’s Bluetooth connection to be disrupted or require manual restarting in some situations. User data can be erased, wifi connectivity can be disabled, and other devices can be interacted with via ACE.
The good news is that BrakTooth only works with Espressif Systems’ ESP32 system on chip (SoC). The bad news is that the ESP32 is widely used in the Internet of Things (IoT) and industrial systems. Because the SoC is so widely used, the researchers’ proof-of-concept exploit employs an ESP32 development kit to carry out assaults on target devices.
BrakTooth was disclosed to all of the impacted vendors, according to the researchers. Some businesses have already published firmware patches to remedy the weakness, while others are investigating it and a few have stated that they will not repair it. Here’s how it works:
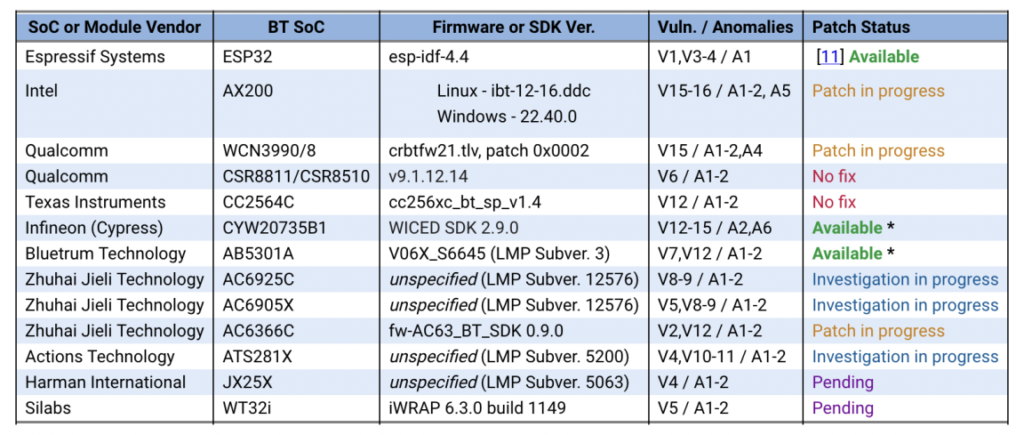
The researchers from the Singapore University of Technology and Design claimed they won’t make the entire proof of concept exploit public until the end of October 2021, when Intel is due to patch its devices. They did, however, release instructions for “a low-cost BT Classic (BR/EDR) Active Sniffer” that will leverage the proof-of-concept vulnerability when it becomes available.
