A new Amazon gift card scam has appeared that aims to capitalise on the increase in online shopping to infect targets with a banking trojan during the holiday season.
Scammers are circulating a highly persuasive phishing email containing a document “weaponized with malicious macros,” according to a study from security firm Cybereason.
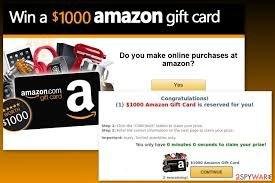
The text, dressed up with Amazon branding, claims to deliver a free $100 voucher to the recipient that they must download to access. They are routed to a legitimate Amazon webpage after the victim has downloaded the file, contributing to the aura of authenticity cultivated by the scammers.
A fearsome banking trojan known as Dridex, intended to steal e-banking credentials and other sensitive information, is the malware installed on the victim’s device. The Trojan, run by the infamous cybercrime syndicate Evil Corp, has been involved since 2012 in various forms.
Operators use three separate distribution methods in this specific instance to infect users with the Dridex trojan: infected Word documents, self-extracting screensaver files, and VBScript files. This variety level maximises the chance to override email security tools that could filter for certain extensions of files.
Amazon Gift Card Scam
This is not the first time scammers have sought to take advantage of consumer interest in trustworthy brands like Amazon, of course, but the increase in e-commerce activity has only added fuel to the fire as a result of the pandemic.
“Consumers have been a preferred target for cybercriminals for a long time, and the sharply increased volume of online shopping spurred by the Covid-19 pandemic has potentially made consumer-focused attacks even more attractive,” explained Cybereason researcher Daniel Frank.

“The fact that Dridex is known to be takedown resistant to some degree, and the fact that there are many other destructive malware variants out there, add to the growing number of online shopping and the associated dangers.”
It is up to all of us to remain alert to social engineering scams, according to Frank, and to investigate any emails that appear too good to be true.
Generally speaking, before entering account or payment details, it is necessary to scrutinise emails for anomalies that may identify a scam (e.g. spelling and grammar errors) and cross-check landing page URLs with known addresses.
On their part, companies should ensure that workers undergo proper safety training and back up this with strict email filters, antivirus software and advanced identity management systems.
