Cybersecurity researchers have observed a new kind of Windows ransomware that was capable of compromising an unpatched Microsoft Exchange email server and make its way into the networks of a US-based hospitality business.
Analysts from Sophos revealed that the ransomware is being called Epsilon Red.
It was first detected by security researchers at Sophos, the ransomware was detected targeting a U.S.-based business in the hospitality industry. According to the cryptocurrency address provided by the attackers, Sophos concluded that at least one of the victims of the Epsilon Red paid a ransom of 4.29BTC or about $210,000, on May 15th.
However, the strangest aspect of the entire campaign is that Epsilon Red’s ransom note closely matches the one dropped by the threat actors behind the REvil ransomware.
“It isn’t clear whether this was enabled by the ProxyLogon exploit or another vulnerability, but it seems likely that the root cause was an unpatched server”. “From that machine, the attackers used WMI to install other software onto machines inside the network that they could reach from the Exchange server.”
The gateway happened to be an enterprise Microsoft Exchange server. The researchers explained,
How does Epsilon Red work?
Epsilon Red is made using Golang (Go), an open-source programming language that is described as easy to build simple, reliable, and efficient but it is led by Powershell Scripts that prepare the target since the ransomware has multiple stages.
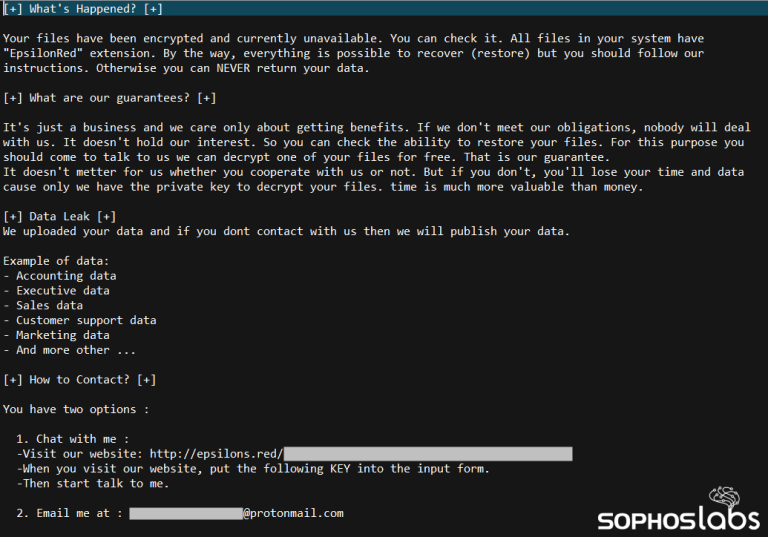
As soon as Epsilon Red makes its way into a machine, it engages Windows Management Instrumentation (WMI) to install other software inside the network, which it accesses from the Exchange server.
Sophos also shared that during the attack, the threat actors launch a series of PowerShell scripts, to prepare the attacked machines for the final stage of ransomware. This involves, for example, deleting the Volume Shadow copies, to ensure that encrypted machines won’t be restored, before ultimately delivering and initiating the actual ransomware itself.
The ransomware itself is rather small and simply encrypts the files since all other phases of the attack are conducted by the PowerShell scripts.
